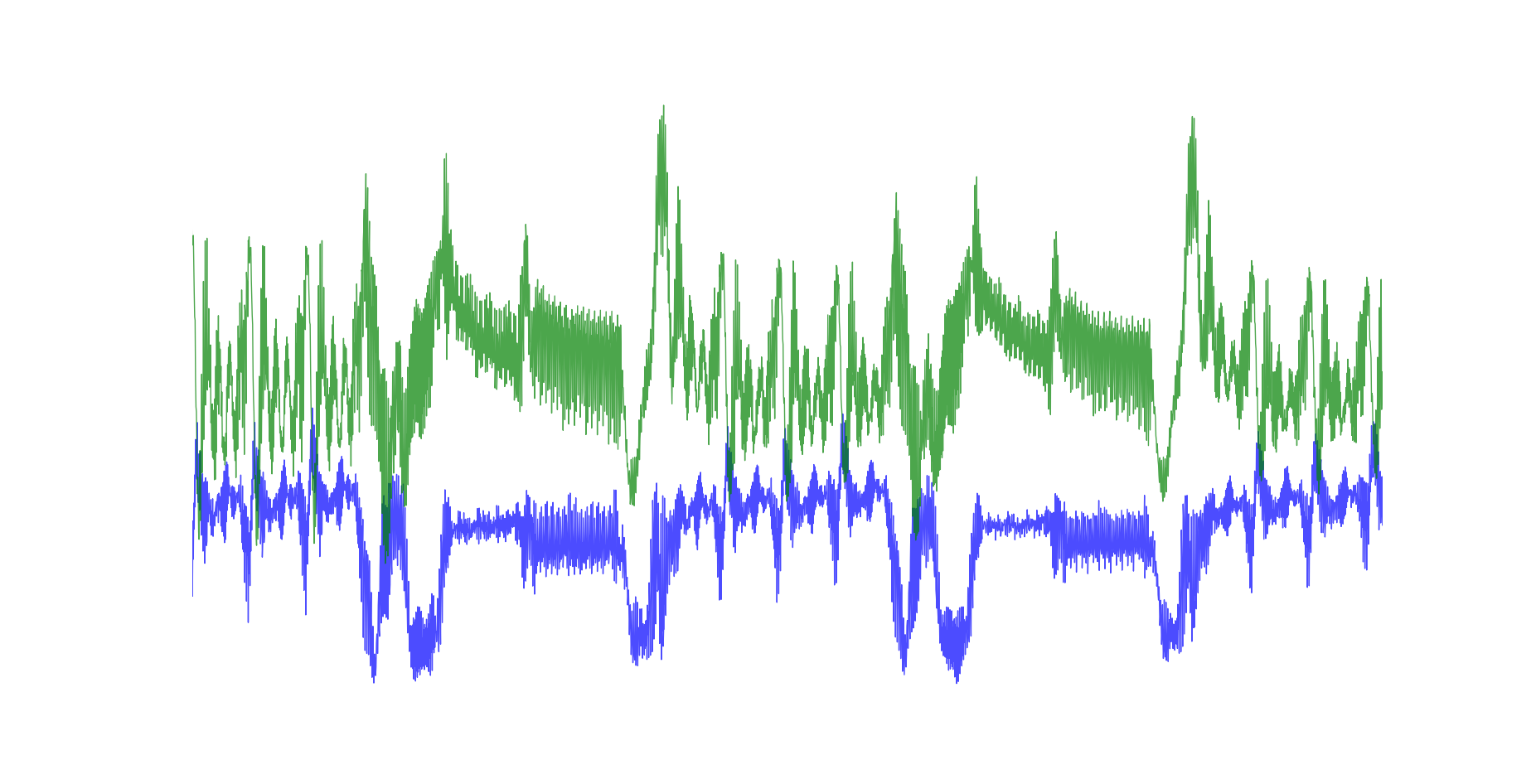
Side channels are communication channels based on execution
characteristics that were not meant to be used for communication.
Characteristics that underly side channels include execution time, power
consumption, and electromagnetic emission. Side channels are known to
be serious threats for cryptography implementations for many years.
Technological improvements usually come with new possibilities for
side-channel
attacks. For instance, the Internet of Things increased the targetable
devices and made the threat more relevant than before.
The lab covers the steps necessary to mount
side-channel attacks against cryptographic implementations, to recover
secret information, and how to mitigate such vulnerabilities:
- implementation of a cryptographic algorithm (AES),
- manipulation of power- and time-traces,
- side-channel leakage model implementation,
- differential side-channel analysis (CPA and LRA),
- extraction of secret key from real-word traces,
- differential side-channel analysis.
- Dozent*in: Damien Marion
- Dozent*in: Alexandra Weber